Account Status:
You are a Tier-1 User. To become eligible for refunds, make at least make at least 6 Purchases. For more information, click here .
Loading...
Loading...
| Seller | Details | Price (USD) | Action | |
|---|---|---|---|---|
How to Hack WiFi Networks WPA2 / WPA3!Description: In this guide, you’ll learn 7 highly effective methods to hack and crack any network. You’ll have an 80%+ success rate if you use all the techniques or just the one that best fits your needs. For both beginners and advanced users. You’ll learn: 0. All requirements: laptop needed, hardware like cards/antennas, etc. 1. Hack using popular Kali Linux frameworks/tools. 2. Launch DoS & Evil Twin attacks to target routers and steal passwords. 3. Silent hacking technique. 4. A fully GUI-based to... 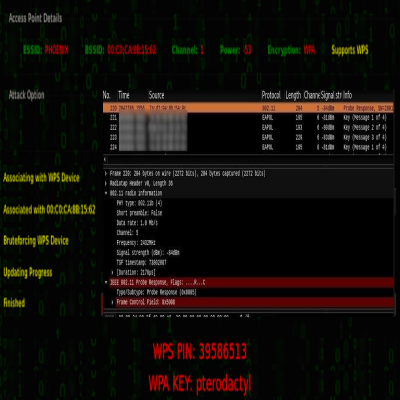
Views:
+100
|
$15.00 | |||
Microsoft Outlook RCE Vulnerability PoCDescription: This script signifies a demonstration (PoC) for CVE-2024-21413, a noteworthy security deficit unmasked in Microsoft Outlook with a CVSS of 9.8. Dubbed the #MonikerLink flaw, this imperfection engenders much-reaching ramifications, including the capacity for the surreptitious divulgence of local NTLM intelligence and the potential for RCE. Furthermore, it delineates an assault trajectory that might bypass Office Protected View, therewith extending its peril to other Office software.
Views:
+50
|
$13.00 | |||
Exploit for OSVDB-75095 | LotusCMS 3.0Description: This is an exploit for the eval() injection vulnerability found ages ago in LotusCMS. Very quick and dirty exploit, written to test out some new ideas I had for writing more streamlined PHP RCE exploits, in this case, using the cookie to set the connectback host/port at runtime when doing a filedropper type thing. I ended up storing the payload itself in a POST variable, as storing it in the cookie lead to some strange encoding issues. See the code for what I mean. The reason for writing this wa...
Views:
+50
|
$5.00 | |||
Windows RCE ExploitsDescription: The exploit samples database is a repository for RCE (remote code execution) exploits and Proof-of-Concepts for WINDOWS, the samples are uploaded for education purposes for red and blue teams. Proof of Concepts are always identified by #PoC# in the name of the relevant exploit folder, and those samples will always pop out a calculator or a message box and therefore will be easily identified by many AV's (which prevent the calculator shellcode). Each sub-category includes a list of folders that...
Views:
+50
|
$3.00 | |||
RCE Exploit for DiamondFoxDescription: Exploit for DiamondFox / Gorynych Botnet C&C Remote Code Execution Exploit. Key features: - Massive Code Cleanup. - Kill-Bots Payload. - Nuke-Stolen-Data Payload.
Views:
+50
|
$5.00 | |||
Public Amazon S3 Buckets [RISK of Data Leakage]Description: The resulting txt file will contain all of the public accessible files from all of the AWS S3 Buckets. At the time of writing this tutorial, I managed to generate a list of over 150,000 files. Just think about it, all of this data is publicly available, now image the amount of damage that this could’ve cause if someone decided that it’ll be a great idea to put sensitive data on there or even worse, a database? Step-by-step guide + scripts included.
Views:
+50
|
$8.00 | |||
UFONet - DDoS Via Web AbuseDescription: What is UFONet? An automatic tool for initiating DDoS attacks, written on Python / GPL v3.0. First edition: -- Born as an XSSer module (2009) -- Started: v0.1b --> 2013 - Exploit Layer 7 (HTTP / Web abuse) -- "Open redirection" vectors OWASP: Top 10 2013-A10- Invalid redirects and referrals - Objective --> Exhaustion of resources (DoS) --------------------------------------------------------------------- NOTE: With your purchase, I’ll include a mini guide on how it works, installation step... 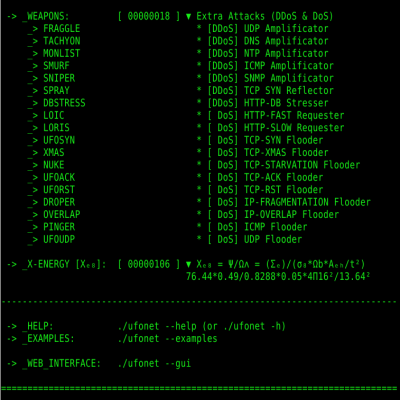
Views:
+100
|
$3.00 | |||
Modlishka Reverse Proxy + Tutorial Bypassing 2FA / OTPDescription: Modlishka is a powerful and flexible HTTP reverse proxy. It implements an entirely new approach of handling HTTP traffic flow, which allows to transparently proxy multi-domain destination TLS traffic over a single domain TLS certificate in an automated manner. What does this exactly mean? In short, it simply has a lot of potential, that can be used in many interesting ways... From the security perspective, Modlishka can be currently used to: - Hijack application HTTP TLS traffic flow through th... 
Views:
+200
|
$10.00 | |||
Microsoft Word Exploit 2025Description: I have observed that this exploit is being sold for over $1,300 USD, as such, I am providing the RAT/builder along with the demonstrative video. Additionally, the builder functions exclusively within Sandbox and VMware. Exploit Specifications: - One-Click .odt Infection Method. - FUD. - Compatible with Email Attachments. - Works on Windows 10/11 & Server 2022/2025. 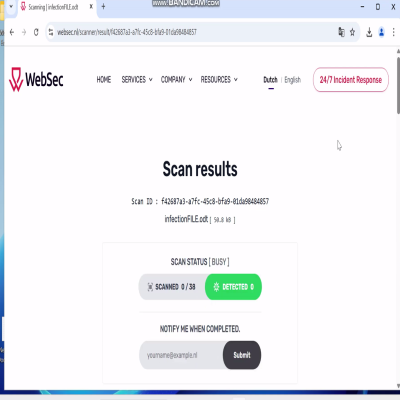
Views:
+100
|
$25.00 |
